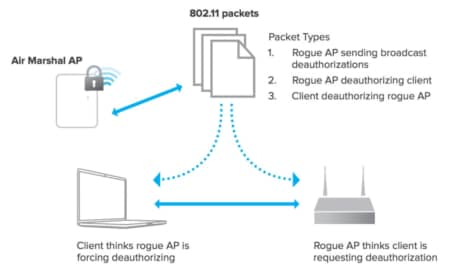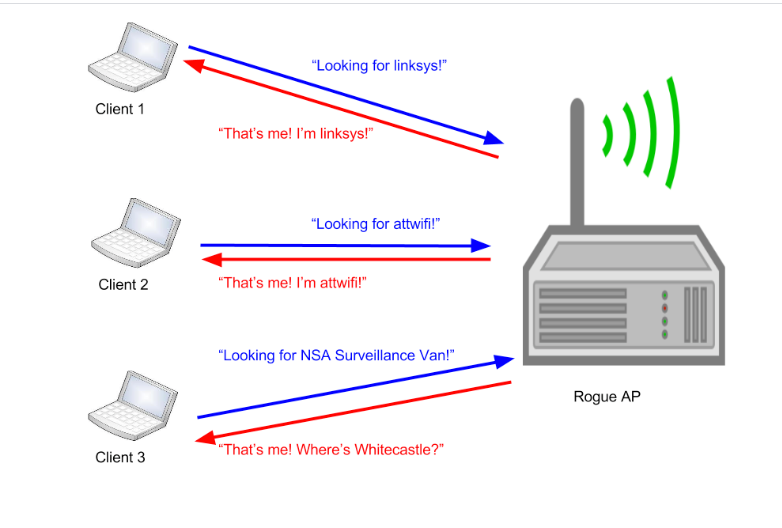
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members

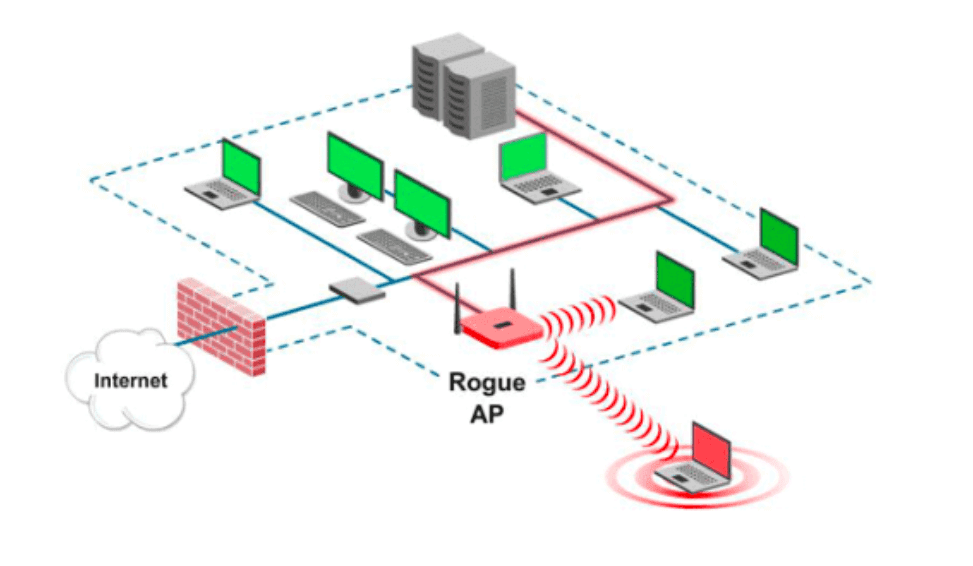
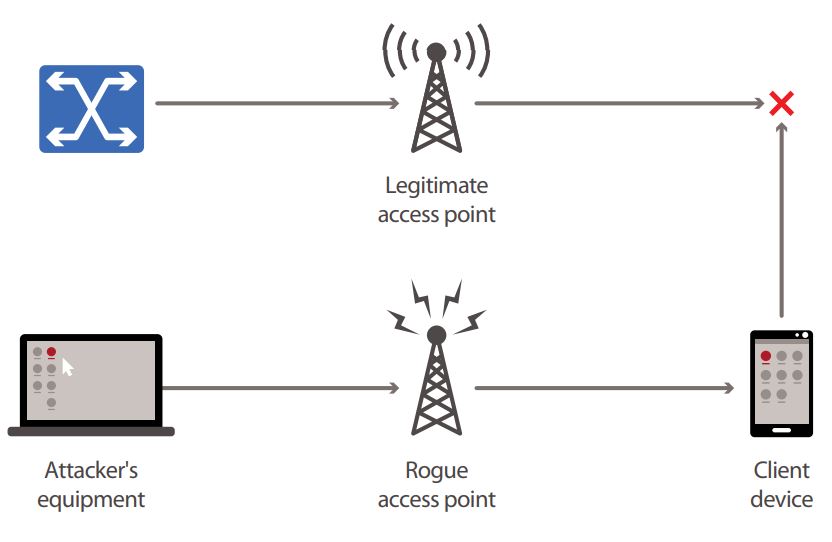
This figure shows the setup of a rogue AP. A rogue AP is connected to... | Download Scientific Diagram

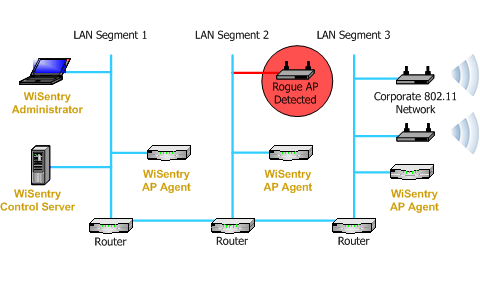
Linksys Official Support - How to enable Rogue AP Detection on your Linksys Wireless-AC Access Point