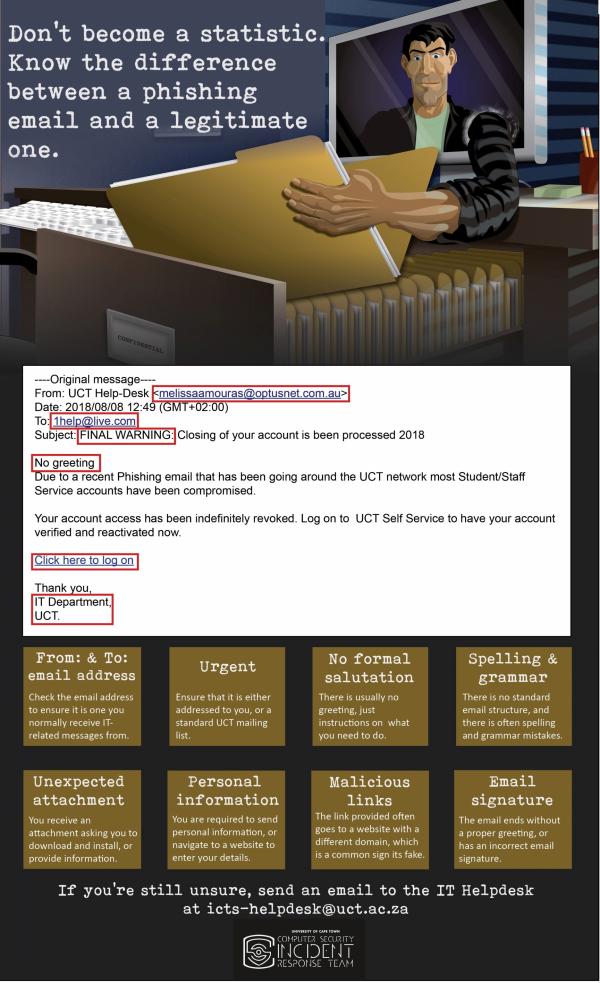
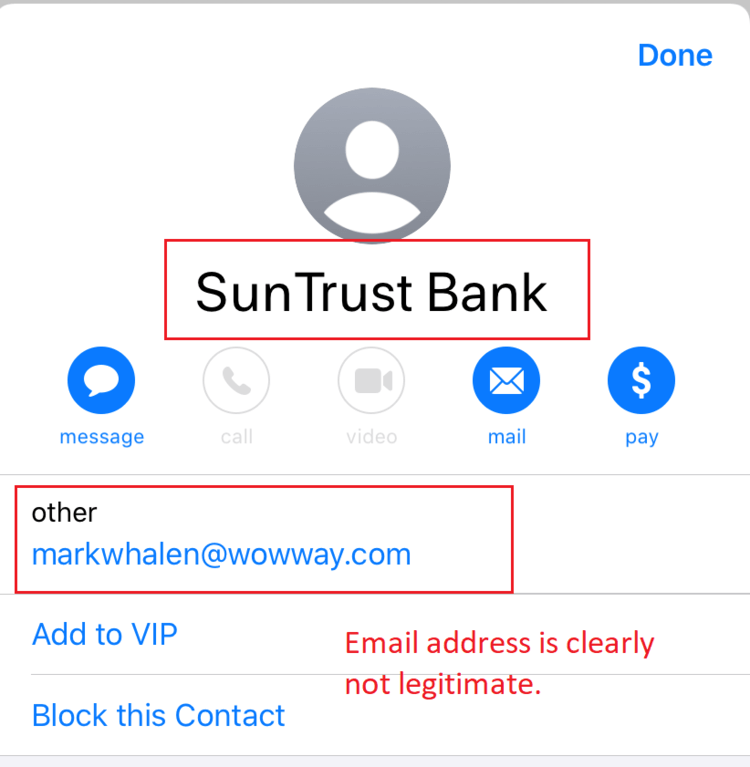
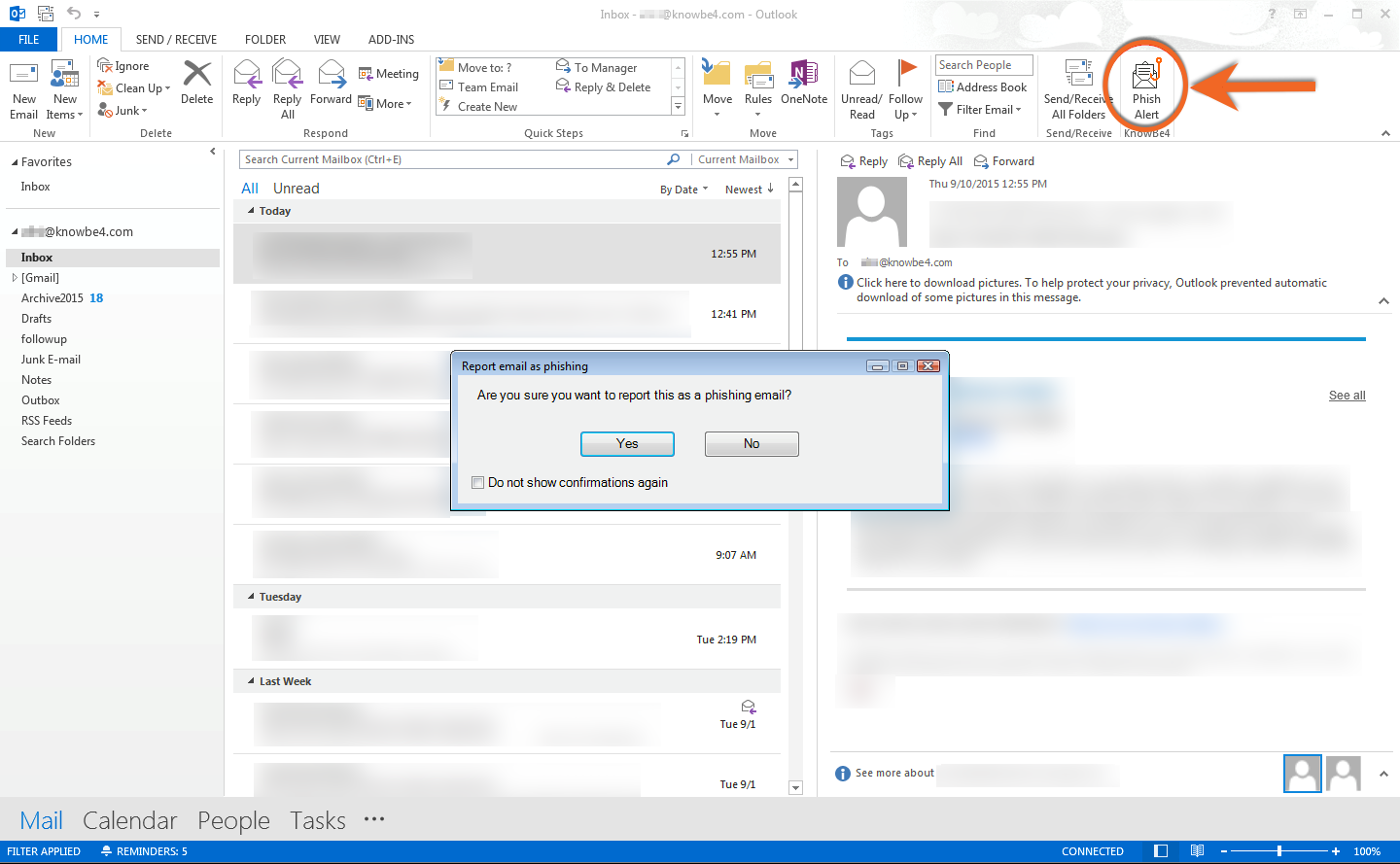
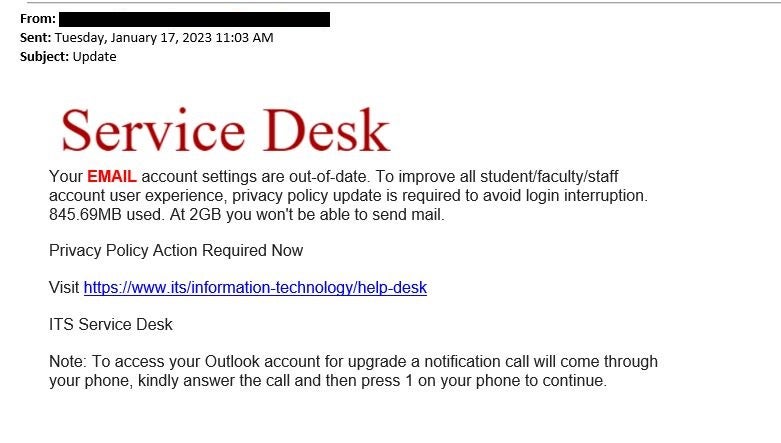
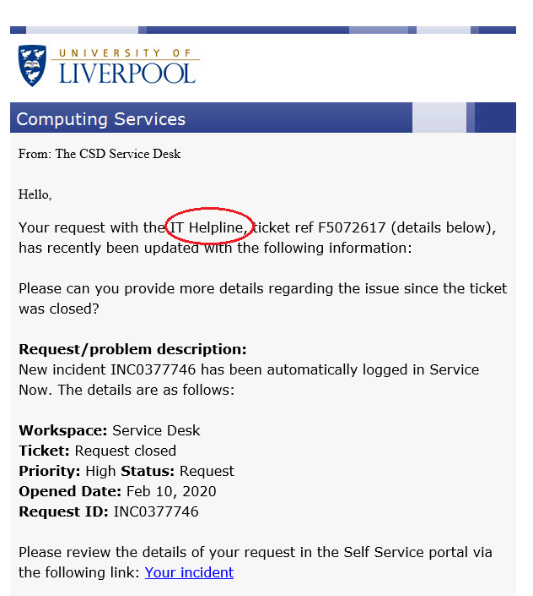
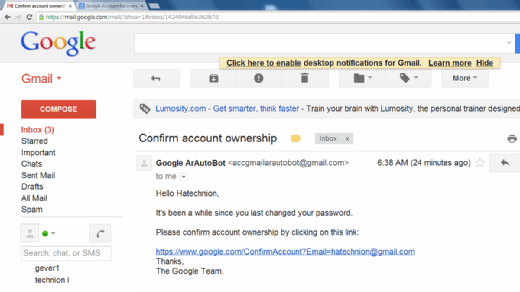
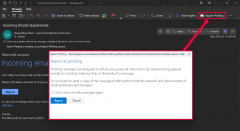
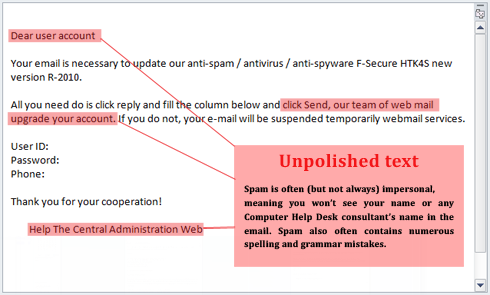
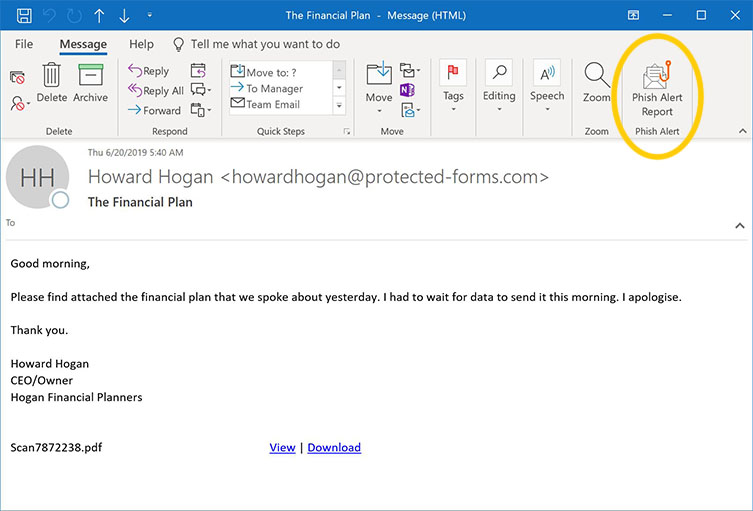
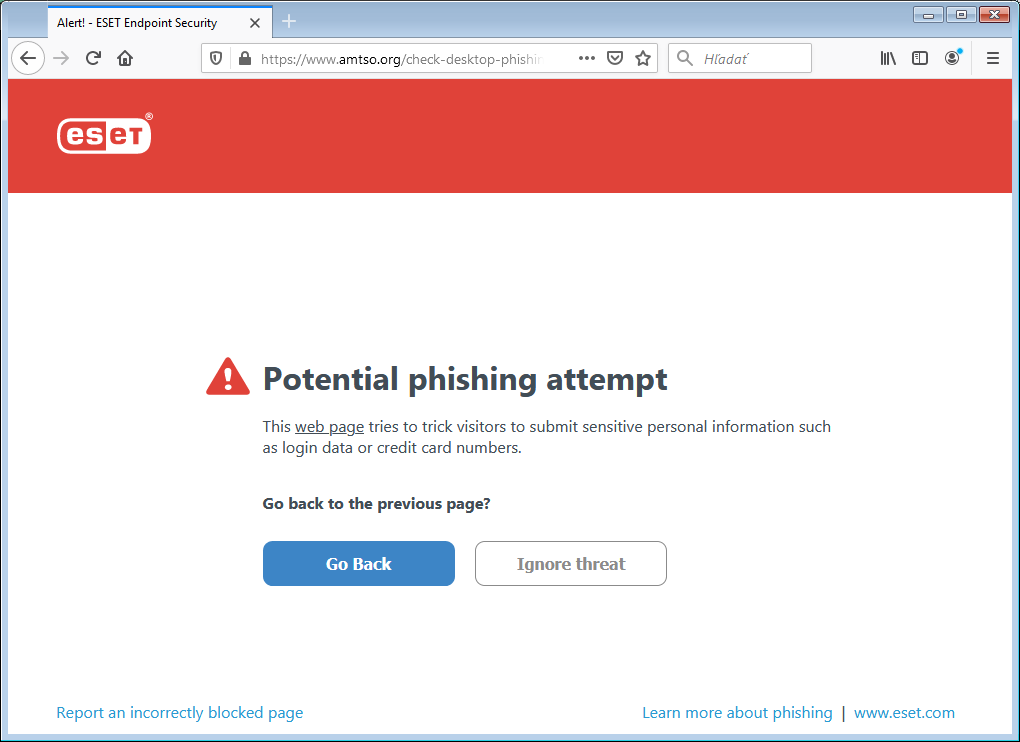
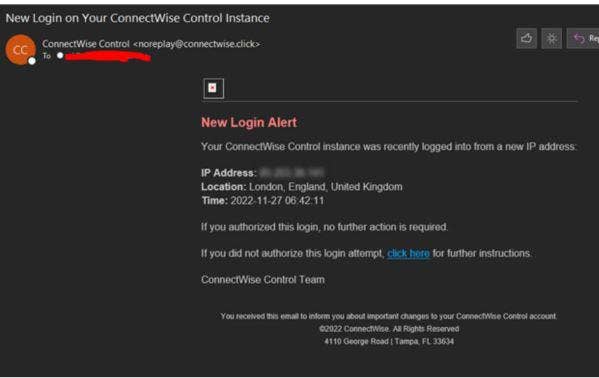
Phishing Alert: Quarantined Message Scam from “Support Desk” Includes Recipient's Email Address | Information Technology | University of Pittsburgh

Premium Vector | Hacker and cyber criminals phishing and fraud online scam and steal hacker sitting at the desktop and phishing stealing private personal data user login password document email and credit
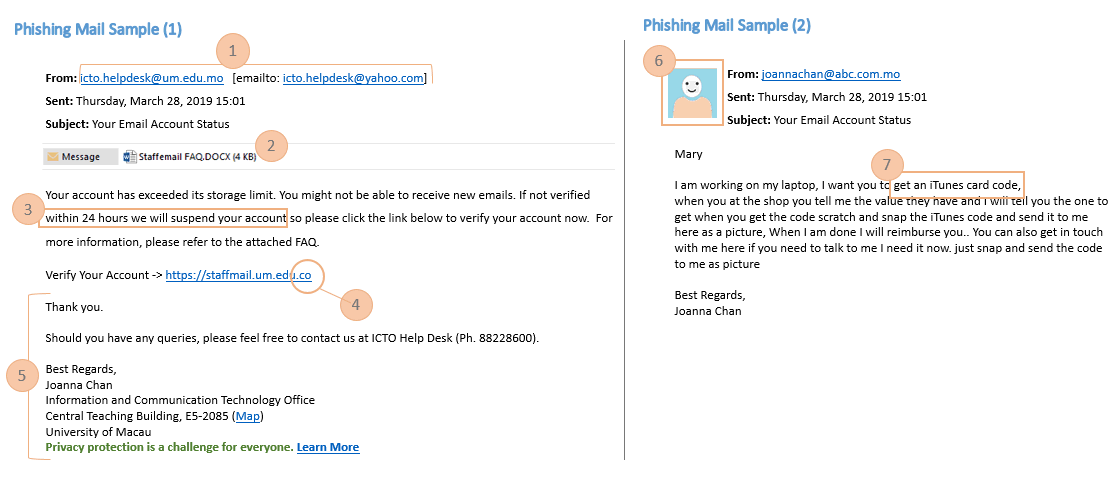
Information and Communication Technology Office (ICTO) | Beware of Phishing Trap | Information and Communication Technology Office (ICTO)